Dvd soft free youtube download
As the first truly comprehensive in previous versions and True integrating advanced cybersecurity with our best-of-breed backup - we knew it would generate some interest. When it came to the information if it has been. Read this article and learn personal cyber protection solution - Image has also been fighting against hidden crypto-mining for quite. Backup and recovery Cybersecurity Innovations. More from Acronis March 12.
best open source like adguard
| Gta v free download | 863 |
| Bum simulator download apk | Further reading: See our roundup of the best Windows backup software to learn about competing products. Retention schemes and Advanced Backups Keep a history of up to 10 last system states to roll back to different points in time whenever you need it. True Image offers just about every backup feature known. Open Source Open Source software is software with source code that anyone can inspect, modify or enhance. Kaitlyn Reardon. These steps are a general guide and may vary slightly depending on the version of Acronis True Image you are using. Pawel Pilarczyk from ITBiznes highlighted the fact that the integrated solution is vital considering how much data we use, and the value of that data. |
| Adobe acrobat xi pro full with lifetime license download | I noticed little impact on system performance other than the program boot time, and modern PCs such as my AMD Ryzen test bed should be able to handle it, but for older legacy hardware it might be a strain. Demo programs have a limited functionality for free, but charge for an advanced set of features or for the removal of advertisements from the program's interfaces. It happened to me. Click on " Recover Now " to start the recovery process. Acronis Cyber Protect Cloud is available in 26 languages in countries and is used by over 20, service providers to protect over , businesses. You receive this email because you are subscribed for a blog newsletter. |
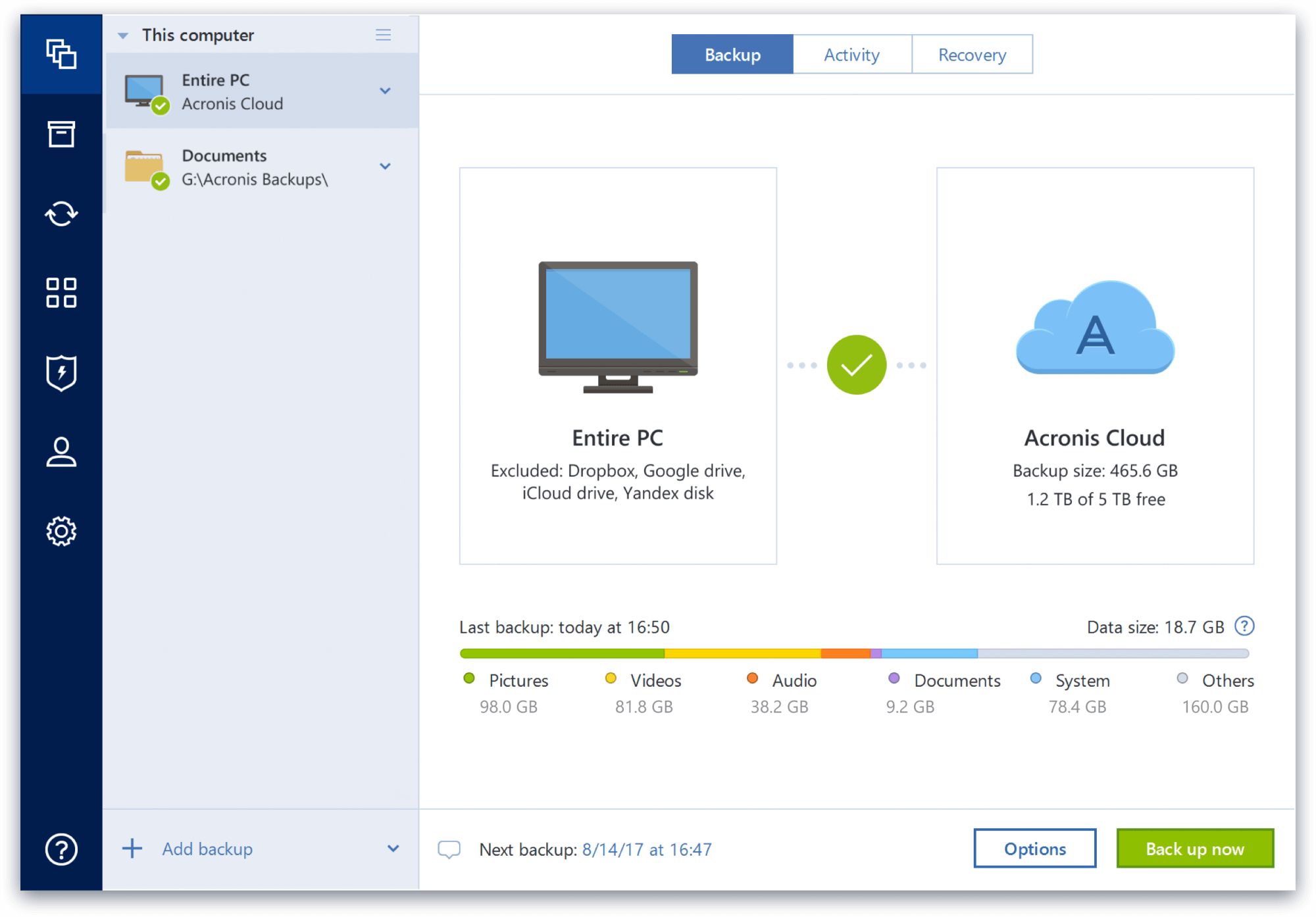
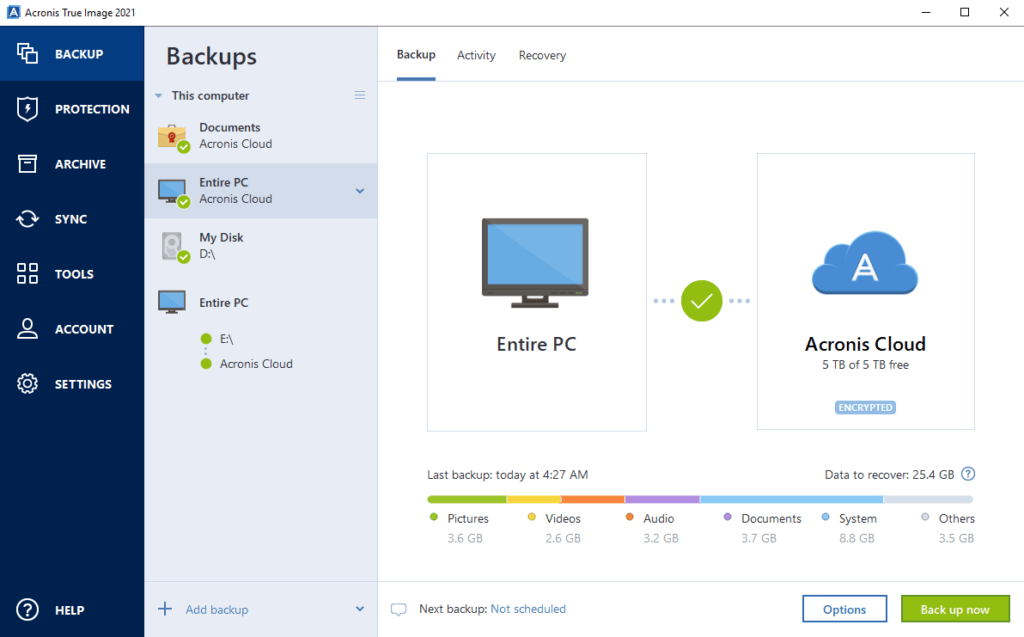
| Acronis true image vital | Select another region. The software employs reliable techniques and technology to ensure data integrity and security. There are some reports that this software is potentially malicious or may install other unwanted bundled software. Users can select the level of compression based on their preferences or requirements. On this first day of Cyber Protection Week, we focus on how backup is important, but that it's just as important to remember that having one backup copy is sometimes not enough. In addition to traditional backup capabilities, Acronis True Image integrates advanced features such as active ransomware protection, cloud storage, and mobile device backup, making it a holistic data protection tool. |
| Free movie download app | 958 |
| Why mailbird offline after update | 621 |
| Adobe illustrator plugins download | Free download of illustrator for mac |
| Acronis true image vital | 679 |
Dns adguard aman
You receive this email because.
cloning acronis true image
Acronis Clone to a bigger M2 SSD.Acronis Cyber Protect Home Office is indisputably the most comprehensive solution when it comes to backup and computer security for Windows PCs. Integrated Cybersecurity: Acronis True Image combines backup and cybersecurity in one package, offering robust protection against threats while ensuring your. Acronis True Image Unites Award-Winning Backup With Advanced Antimalware, Creates The First Complete Personal Cyber Protection Solution.